Incident Response Plans
Ensuring Robust Cybersecurity Across Defense, Healthcare, Manufacturing, and Pharmaceutical Sectors
Having a robust Incident Response Plan (IRP) is no longer optional—it's imperative. As a premier Managed Security Service Provider (MSSP), Dragnet’s mission is to deliver defense-grade cybersecurity solutions to all. And as every good soldier knows, when you are under siege, you need to make sure you have a battle plan.
Understanding Incident Response Plans
An Incident Response Plan is a structured set of procedures that an organization follows when dealing with a security breach or cyberattack. It enables the organization to quickly detect, contain, and recover from the incident, thereby minimizing damage and impact on operations. A well-crafted IRP ensures a coordinated response from relevant teams and helps maintain business continuity.
Key Aspects of an Incident Response Plan
Assigning Roles and Responsibilities:
Clearly outline who is responsible for different tasks during an incident, such as investigation, communication, and system restoration.
Identifying Potential Incidents:
Defining what constitutes a security incident and how to recognize it.
Escalation Procedures:
Establishing a process for escalating incidents based on severity to the appropriate personnel.

Communication Strategy:
Defining how to communicate with stakeholders, including employees, customers, and regulatory bodies, during an incident.
Data Collection and Analysis:
Outlining methods for gathering and analyzing relevant data to understand the scope of the attack.
Containment and Mitigation Actions:
Defining steps to isolate compromised systems and prevent further damage.
Recovery and Restoration Process:
Establishing procedures to restore affected systems and data to operational status.
The Evolution of Cybersecurity Regulations
Regulations such as the Defense Federal Acquisition Regulation Supplement (DFARS) and the Cybersecurity Maturity Model Certification (CMMC) have been pivotal in shaping the cybersecurity landscape for defense contractors and subcontractors. The DFARS requirements, finalized on October 21, 2016, imposed safeguarding and cyber incident reporting obligations on defense contractors. However, from 2015-2017, an audit firm found that the typical contractor was only approximately 60% compliant with DFARS clause 252.204-7012.
The introduction of CMMC in January 2020, with versions 1.0 and later 2.0, has streamlined the cybersecurity requirements, aiming to ensure that defense contractors and subcontractors adhere to stringent cybersecurity standards. The U.S Department of Defense (DoD) finalized the CMMC Program rule on October 15, 2024. The CMMC program requires defense contractors to meet cybersecurity requirements based on the sensitivity of the information they handle. The program will use a three-level system: Level 1 (Foundational), Level 2 (Advanced), and Level 3 (Expert). The DoD will eventually include CMMC requirements in all applicable contracts but plans to roll out the requirements in phases over three years. The effective date of the rule may be early 2025.
Incident Response Plans and CMMC:
An incident response plan is crucial for achieving CMMC compliance as it outlines the structured process for detecting, responding to, and recovering from cybersecurity incidents, ensuring an organization can effectively handle potential breaches and minimize damage by having clear procedures in place to identify threats, contain them, and restore systems to normal operation; essentially, CMMC requires organizations to have a robust incident response capability, including planning, training, and testing to be able to react appropriately to security incidents.
Essential for compliance:
CMMC levels 2 and above mandate a well-defined incident response plan to address potential cyber threats and demonstrate the ability to handle security incidents effectively.
Key components:
A CMMC-compliant incident response plan should include elements like incident detection methods, containment strategies, eradication procedures, data recovery plans, and post-incident analysis to prevent future occurrences.
Training and awareness:
CMMC emphasizes training employees at all levels to recognize and report potential incidents, which is a crucial part of an effective incident response plan.
Reporting requirements:
Organizations must have clear protocols for reporting incidents to relevant stakeholders, including the Department of Defense (DoD) if applicable, as per CMMC guidelines.
Testing and Evaluation:
CMMC compliance necessitates regularly testing the incident response plan to identify weaknesses and ensure its effectiveness in real-world scenarios.
How to Implement an Incident Response Plan for CMMC
Identify critical assets:
Determine which systems and data are most sensitive and require priority protection in case of an incident.
Establish detection mechanisms:
Implement monitoring tools and processes to identify potential security breaches early, such as log analysis, network traffic monitoring, and user activity monitoring.
Define roles and responsibilities:
Assign clear roles to different team members, including incident responders, communicators, technical experts, and leadership, to facilitate coordinated response.
Develop response procedures:
Create detailed steps for each stage of incident response, including initial detection, containment, eradication, recovery, and post-incident review.
Conduct regular training:
Train employees on how to recognize potential incidents, report suspicious activity, and follow established response procedures.
Benefits of an Incident Response Plan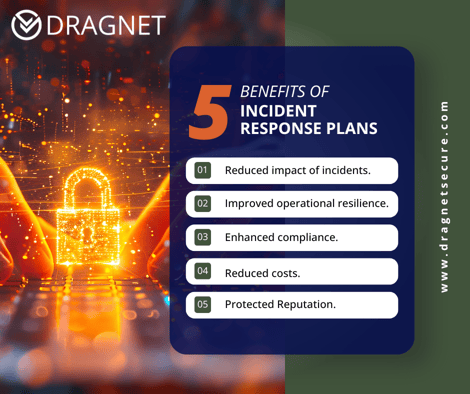
Implementing a comprehensive Incident Response Plan offers numerous advantages:
Reduced Impact of Incidents:
Organizations can react quickly and effectively to minimize damage from a security breach.
Improved Operational Resilience:
A well-defined plan helps organizations maintain business continuity during a disruption.
Enhanced Compliance:
Demonstrates adherence to relevant data protection and cybersecurity regulations.
Cost Reduction:
Early detection and response can help limit financial losses associated with a breach.
Reputation Protection:
Effective incident response can mitigate negative impact on an organization's public image.
At Dragnet, we are your tactical team armed and ready to help you make sure you are battle ready. We offer a suite of cybersecurity services tailored to meet the unique needs of defense contractors, healthcare, manufacturing, and pharmaceutical industries. Our services include:
- Gap and Risk Assessments: Identify vulnerabilities and assess risks to develop a strategic cybersecurity roadmap.
- CMMC/NIST Program Management: Ensure compliance with CMMC and NIST standards through comprehensive program management.
- Penetration Testing: Simulate cyberattacks to evaluate the security posture and identify weaknesses.
Embrace the future with confidence by partnering with us to safeguard your critical assets. Our defense-grade cybersecurity solutions are designed to protect your organization from the ever-evolving cyber threats, ensuring operational continuity and regulatory compliance.
You May Also Like
These Related Stories
.png)
CMMC 2.0 Goes into Effect on December 16, 2024
.png)
CMMC: The Cybersecurity Maturity Model Certification
.png)


